Wednesday, April 10th, 2019
Zeus Banking Trojan: Malware Review

This week at Smarttech247 our technical teams have been discussing the Zeus banking trojan, aka Zbot, which uses keystroke logging to compromise victims’ credentials when users visit a banking website. Zeus was first seen in 2007 and was made freely available to the public by its creator in 2011. Its objective? To steal banking information for financial gain. It can be delivered to devices through 3 methods: phishing, spam and drive-by download. The initial impact when the malware started its infiltration affected more than 3.6 million PCs in the United States causing over $70 million in damages. Anyone using a Windows PC can fall victim to the Zeus virus, even with up-to-date antivirus, it can be near impossible to detect.
How it Works
Since created, Zeus has been the reason for millions of infected PCs and it has been used to steal data from organisations such as NASA, Monster.com, Oracle, Cisco and Amazon. It was designed to harvest banking credentials from the computers it infects by monitoring the websites its users visit and keystroke logging. When the virus recognises the user is on a banking website, it will record the keys pressed in order to log into the website, saving the credentials.
The virus can also act as a botnet allowing the individual to extract large amounts of data and execute large scale attacks by commanding a large network of infiltrated devices.
As earlier stated, the attacks usually infect in three ways: phishing, spam and drive-by download. The phishing emails are often customised to fool employees to make it look as though the email is coming from within the organisation they are working for. The email will often be targeted at system administrators or management level employees in the hope they may log onto the system the hacker wants access to.
Delivery
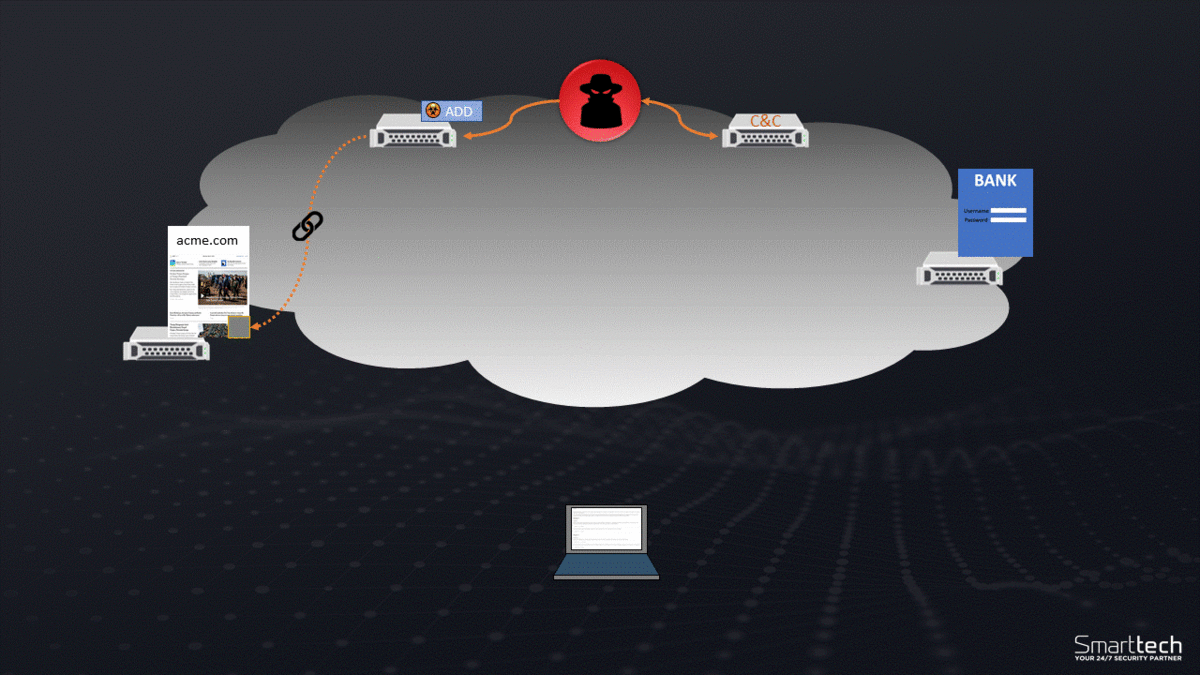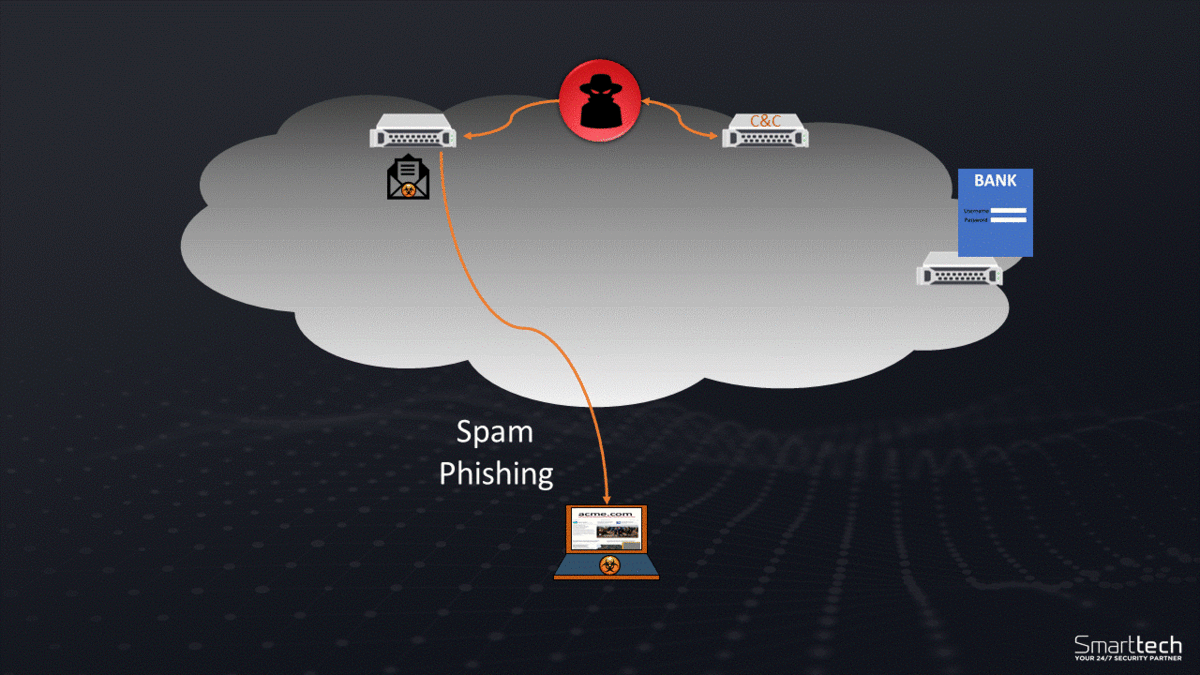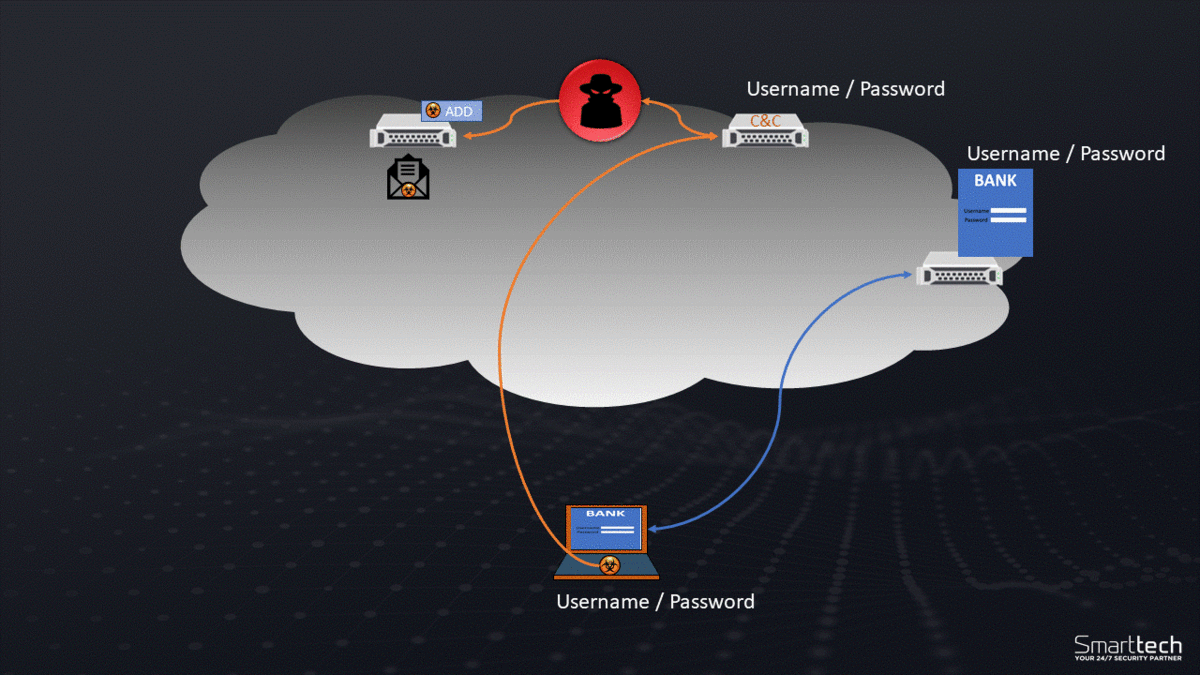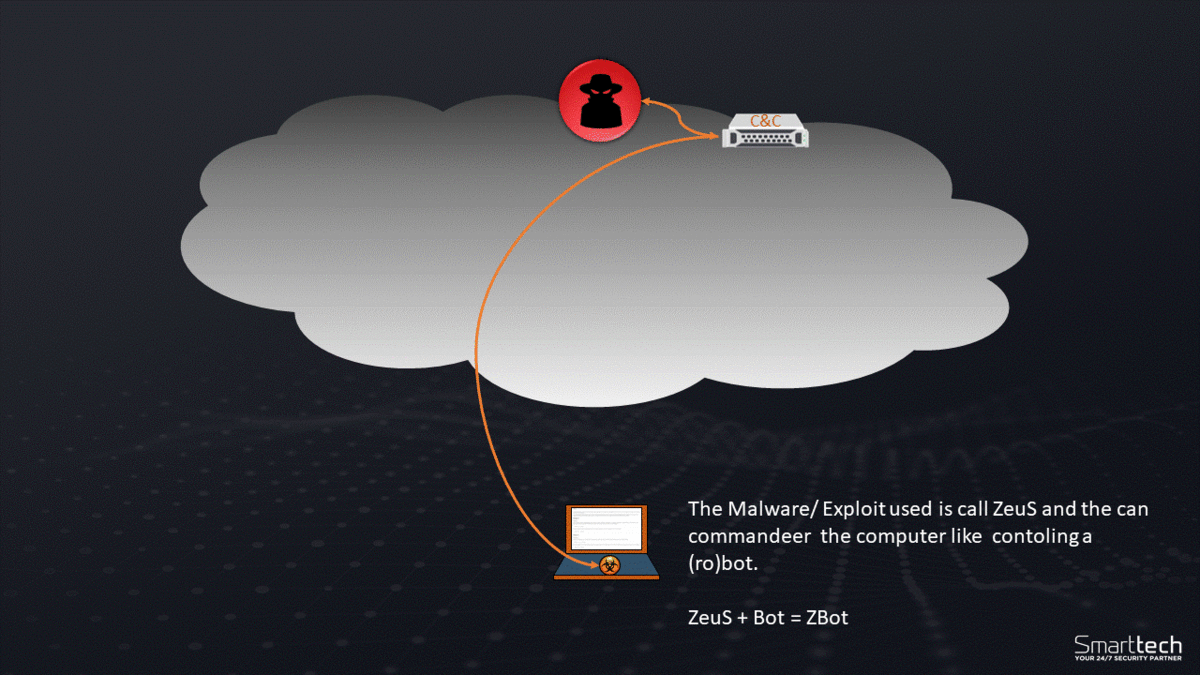
The attack can also be found to arrive in spam, both emails and social media messaging. A link is contained within the email or social media post that once it is clicked, the user is directed to a website that automatically installs the virus. The virus is created to steal credentials so will often steal the credentials of the email and social media accounts used to click the link to further spread the message from what you may think is a ‘trusted’ source.
The final way the virus uses to infect devices is through a drive-by download. Hackers are able to contaminate legitimate websites that the user may have used before to automatically download the virus file and execute it on the device.
The Zeus virus initially only affected Windows computers but there have been instances that affect Android, Blackberry and Symbian devices. The creator of the virus made the Zeus source code publicly available in 2011, allowing for the creation of a number of new, updated instances of the malware. Even though the original Zeus malware has been largely neutralized, the Trojan lives on as its mechanisms are used in a large number of new malware types.
Protection
Protecting yourself from the Zeus banking trojan virus can be difficult as it can be impossible to detect. The most logical first step is keeping your antivirus up-to-date, and run regular full scans. Ensure you educate your staff to detect phishing and what to do if they aren’t sure of an email. Never click on suspicious links be it on social media or in email.
Contact Us
The data you supply here will not be added to any mailing list or given to any third party providers without further consent. View our Privacy Policy for more information.