Wednesday, January 24th, 2018
Effective Security Response Strategy – 6 Steps

Cyber incidents have been on an exponential rise in both number and sophistication for the past few years and require an effective response strategy. These incidents arrive in the form of denial of service attacks, data exfiltration and encryption. 2017, for instance, saw quite a number of malware incidents, some of which ended up crippling business processes and bringing several daily activities to a total standstill. Two of our favourite examples are the WannaCry and Non-Petya ransomware. Cyber incidents threaten the security, confidentiality, integrity, or availability of an organisation’s information assets, systems, and/or networks that deliver the information. Any form of system policy, acceptable use policy or computer standard practice violation, therefore, has to be treated as an incident. Some popular examples of typical incidents are an unauthorised entry, denial of service, malicious code or virus, unauthorised scan/probe.
Examples
“File A now reads as xysjdsndhd.exe! File B converting to hsdssdjsdjs.pdf
Mary cannot get any file to open on her system!
Is she the only one? John’s PC in accounting is experiencing the same issues! Lucy in HR also!!
Oh great! We have just been hit with Ransomware!”
Response Strategy
What happens in moments like the scenario described above, when your organisation’s security has been breached and the integrity, availability, and confidentiality of your systems have been compromised? How should your organisation respond? Here are five effective and practical steps to create and maintain a proper and actionable response strategy:
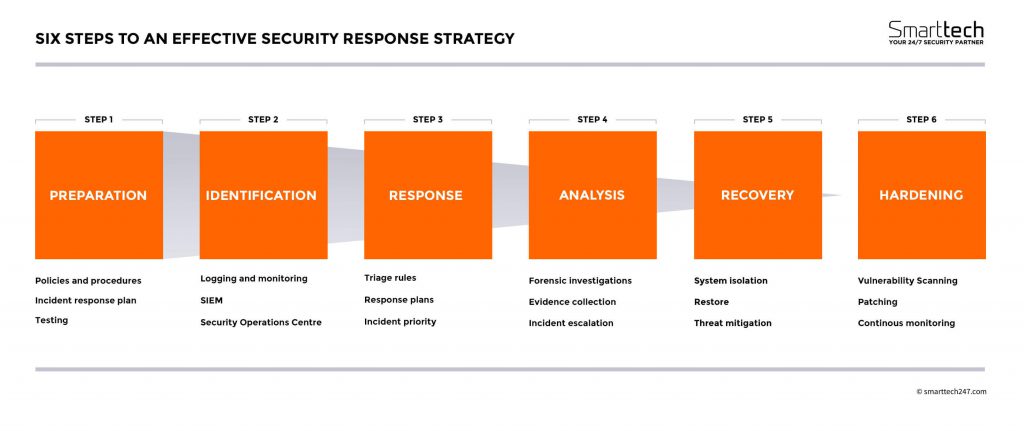
-
Preparation
Preparation is the most important step in an effective incident response plan. It is important for an organisation to have a clearly written, unambiguous incident response plan and policy. “What do we do when X happens?” “Who handles what?”. Policies must be in place to manage any form of cyber incidents. They must be updated regularly depending on the organisation’s policies and the criticality of the data and systems they handle. All policies and plans should be regularly tested by the organisation’s management. This ensures that the process of recovery is completed in a fast and painless manner, leaving the organisation with the least amount of damage as possible. Ensure the right tools and personnel are also available to swing into action when a cyber incident occurs.
-
Identification
It is very important to have tools in place in order to detect potential incidents. These tools should monitor all forms of logs in real-time and scan for all manner of vulnerabilities. By monitoring a network and incorporating threat intelligence feeds it is more manageable and faster to detect potential security incidents.
Depending on the criticality of the systems involved, monitoring can range from a system administrator looking through system event logs to having a small monitoring centre inside the organisation, even up to contracting a dedicated security operations centre for network monitoring. For example, Smarttech247 has a dedicated security operations centre using IBM QRadar SIEM (security information and event management) for dedicated network monitoring for our customers which also incorporates artificial intelligence in the form of IBM Watson for cybersecurity.
By using a dedicated security operation centre, organisations can leave the network monitoring and incident handling to dedicated security professionals. However, whatever method an organisation opts for, there has to be some form of network monitoring, one way or the other. After detecting, it is important to carefully and correctly identify what kind of incident has occurred and on what subnet and hosts (as the case may be) have they occurred in. Has there been a loss of data and confidential information? Are the critical assets involved? How much impact has it had on the network?
-
Response
Speed is a key factor in responding to incidents. The faster an organisation responds to a security incident, the less damage it is likely to result in and the less impact it will have on critical assets and infrastructures. It is good practice to have proper triage rules already clearly spelled out in response policies and procedures. What level of priority should be given to what of kind of incidents? Triage rules should primarily be based on the risk level of the affected systems or the incident.
Questions such as ‘will this bring down critical systems?’ or ‘will this compromise the integrity or confidentiality of our systems?’ must be answered while determining triage levels. For example, a hospital might want to assign a Priority 1 (highest priority) to a ransomware attack and a Priority 3 to communication with a known malicious IP address etc. Depending on proper identification of the incident, a proper response plan can then be followed. A typical scenario is in the case of a malware attack is that the affected systems are usually first isolated before any further analysis.
-
Analysis
It is very important for an organisation to have experts analysing security incidents from the moment they occur. Evidence should be collected and analysed by security analysts and further escalated as deemed fit. Remove all forms of malicious code, threats, and factors responsible for the incidents.
For example, in the case of communication with a malicious IP address, the analyst might simply need to block that IP on the firewall and scan the localhost involved with various anti-virus solutions to ensure no infection has occurred, but in the case of a critical malware (let’s say ransomware) attack, or data loss/ data transfer, an analyst might need to escalate it to more technical levels such as going on site, taking bit-to-bit images of affected systems and carrying out further digital forensic investigations. It is important to critically analyse all that can be analysed in relation to an incident. From the endpoint logs to making a bit-for-bit system image. This step must be done by individuals highly skilled in memory analysis, malware analysis, digital forensic investigation and security analysis.
-
Recovery
It is important to get the systems running as fast as possible with the least amount of damage that can be achieved. Carry out the recommended actions as considered fit, depending on the incident. Isolate and wipe infected systems and restore data from backups available. Ensure all forms of malicious IP addresses involved are blocked (command and control servers, etc.) and stopped from further communicating with your network. These are known threat mitigation actions. Only after the system is restored and the threat has been fully quashed should it come back to action. It is important a skilled security professional coordinates this step in incident response. The strategies used in this phase are primarily dependent on the intelligence gathered during the analysis stage and the method of compromise.
-
Hardening
Ensure your data is continually backed up. Create new security initiatives to ensure future incidents of that kind does not occur again. For example, one of the actions we carry out at Smarttech247 after responding to an incident is to create rules in QRadar to continually monitor and check for any signs or indicators of the particular incident and set alerts for it. By doing this, we are able to keep track of the particular incident and ensure it doesn’t happen again. Continuous monitoring of that incident must occur. It is also important to keep the systems properly patched and up to date with a scheduled vulnerability scanning/ patching if none exists.
Finally, it is very important to document every single step throughout an incident response and update the incident report plan after (if necessary). This will help in improving the incident response plan and inproper documentation of events. What happened and how was it stopped? What could have been done to prevent it in the first place?
In protecting your organisation’s security posture, preparation is just as important as preventing a cyber incident from ooccurring in the first place. The question has moved from “what will we do if we experience a security incident” to “what will we do when we experience a security incident”.
This topic, among others, will be thoroughly discussed by industry experts at Zero Day Con in Dublin on March 7th, 2018.
Contact Us
The data you supply here will not be added to any mailing list or given to any third party providers without further consent. View our Privacy Policy for more information.