Thursday, March 11th, 2021
Microsoft Exchange – Exploitation of vulnerabilities

Summary from the Joint Cybersecurity Advisory between the FBI and CISA on Microsoft Exchange
An advisory was created by the Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) to highlight the cyber threat associated with active exploitation of vulnerabilities in Microsoft Exchange on-premises products. The FBI and CISA assessed that nation-state actors and cyber criminals are likely among those exploiting these vulnerabilities.
The exploitation of Microsoft Exchange on-premises products poses a serious risk to Federal Civilian Executive Branch agencies and private companies. Successful exploitation of these vulnerabilities allows an attacker to access victims’ Exchange Servers, enabling them to gain persistent system access and control of an enterprise network. It has the potential to affect tens of thousands of systems in the United States and provides adversaries with access to networks containing valuable research, technology, personally identifiable information (PII), and other sensitive information from entities in multiple U.S. sectors. FBI and CISA assessed that adversaries will continue to exploit this vulnerability to compromise networks and steal information, encrypt data for ransom, or even execute a destructive attack. Adversaries may also sell access to compromised networks on the dark web.
On March 2, 2021, Microsoft and Volexity announced the detection of multiple zero-day exploits used to target vulnerabilities in on-premises versions of Microsoft Exchange Servers. In light of this public announcement, FBI and CISA assess that other capable cyber actors are attempting to exploit these vulnerabilities before victims implement the Microsoft updates. The FBI is proactively investigating this malicious cyber activity, leveraging specially trained cyber squads and CyWatch, the FBI’s 24/7 operations center and watch floor, which provides around-the-clock support to track incidents and communicate with field offices across the country and partner agencies.
Technical Details
On March 2, 2021, Microsoft released security updates for several zero-day exploits (CVE 2021- 26855, CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065). Continual use of unpatched exchange servers or delayed implementation of Microsoft-released updates poses a serious risk to affected systems. It is highly likely that malicious cyber actors will continue to use the aforementioned exploits to target and compromise the networks of U.S. entities for cyber-enabled espionage, data exfiltration, and criminal activity.
Log File Analysis
Any file below the following file path can be targeted with XML SOAP POST requests for unauthenticated execution. Check log files for POST requests to these resources:
/owa/auth/Current/themes/resources/*
Example file paths targeted:
- /owa/auth/Current/themes/resources/logon.css
- /owa/auth/Current/themes/resources/owafont_ja.css
- /owa/auth/Current/themes/resources/lgnbotl.gif
- /owa/auth/Current/themes/resources/owafont_ko.css
- /owa/auth/Current/themes/resources/SegoeUI-SemiBold.eot
- /owa/auth/Current/themes/resources/SegoeUI-SemiLight.ttf
- /owa/auth/Current/themes/resources/lgnbotl.gif
Check Exchange ECP server logs for the following:
S:CMD=Set-OabVirtualDirectory.ExternalUrl=
Note: ECP Server logs are typically located at \Logging\ECP\Server\.
Check IIS logs for access to the following resource (this resource can be used legitimately, but should be noted):
/ecp/DDI/DDIService.svc/SetObject
PowerShell Commands
Running the PowerShell commands below on an Exchange server can help detect evidence that the following CVE’s may have been exploited:
Detect Possible CVE-2021-26855 Exploitation
Import-Csv -Path (Get-ChildItem -Recurse -Path “$env:PROGRAMFILES\Microsoft\Exchange Server\V15\Logging\HttpProxy” -Filter ‘*.log’).FullName | Where-Object { $_.AuthenticatedUser -eq ” -and $_.AnchorMailbox -like ‘ServerInfo~*/*’ } | select DateTime, AnchorMailbox
Detect Possible CVE-2021-26858 Exploitation
findstr /snip /c:”Download failed and temporary file” “%PROGRAMFILES%\Microsoft\Exchange Server\V15\Logging\OABGeneratorLog\*.log”
Detect Possible CVE-2021-26857 Exploitation
Get-EventLog -LogName Application -Source “MSExchange Unified Messaging” – EntryType Error | Where-Object { $_.Message -like “*System.InvalidCastException*” }
Detect Possible CVE-2021-27065 Exploitation
Select-String -Path “$env:PROGRAMFILES\Microsoft\Exchange Server\V15\Logging\ECP\Server\*.log” -Pattern ‘Set-.+VirtualDirectory’
Note: additional advanced SIEM hunting queries are available in the Microsoft Blog: HAFNIUM targeting Exchange Servers with 0-day exploits to help identify initial exploitation.
TTPs Identified:
- Webshells (ASPX and PHP)
- rundll32 C:\windows\system32\comsvcs.dll MiniDump lsass.dmp
- PsExec
- ProcDump
- WinRar Command Line Utility
- 7zip • PowerCat (Github)
- Nishang (Github)
- Adding and using PowerShell Snap-Ins (Add-PSSnapin) to export mailboxes (GetMailboxExportRequest)
Additional/Deletion of Domain User Accounts/Groups can be found in the full report. Advisory Summary
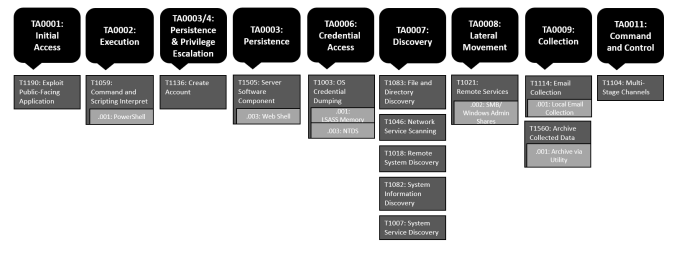
ATT&CK PROFILE
Summary of the MITRE ATT&CK techniques observed.
Mitigations
Compromise Mitigations Organizations that identify any activity related to Microsoft Exchange Server indicators of compromise (IOCs) within their networks should take action immediately by following the process oulined in the FBI & CISA report.
Smarttech247 recommend applying Microsoft‘s security fixes immediately. However, just because fixes are applied now, this does not mean that servers have not already been compromised.
Smarttech247 will continue to support our customers, partners and the security community the best we can from threat actors who work tirelessly to steal data, extort and cause harm.
Contact Us
The data you supply here will not be added to any mailing list or given to any third party providers without further consent. View our Privacy Policy for more information.